"Volume Shadow Copy"(VSS/VSC) is important artifacts for examiners because it stores previous data as snapshots.
Some malware delete this "Shadow Copy"(SC) on purpose. The following site reports that they wipe files such as private key or its component by "SDelete", then delete SC by wmic command.
CRYPVAULT: New Crypto-ransomware Encrypts and “Quarantines” Files
http://blog.trendmicro.com/trendlabs-security-intelligence/crypvault-new-crypto-ransomware-encrypts-and-quarantines-files/
Another report describes that they delete SC by vssadmin command.
CryptoWall 3.0 Ransomware Partners With FAREIT Spyware
http://blog.trendmicro.com/trendlabs-security-intelligence/cryptowall-3-0-ransomware-partners-with-fareit-spyware/
So I have checked out what is happening on disk when SC was deleted. Specifically, I focused whether it would be possible to recover data from deleted SC.
In my conclusion, deletion SC by wmic/vssadmin is just a deletion process for file system layer. So the contents are untouched until another file overwrites the corresponding area. In that case, you can recover the data if you choose the appropriate methods/tools.
My validation process is as follows:
At first, I prepared virtual disk containing recoverable data from SC.
- I created 3 files named "0B.bin"(100MB), "A0.bin"(5MB) and "FA.bin"(100MB) on disk. These contents of files are "0x0b 0x0b...", "0xa0 0xa0..." and "0xfa 0xfa..." respectively.
- I created system restore point via control panel manually.
- I wiped these 3 files by SDelete command.
- I created image file of this virtual disk.
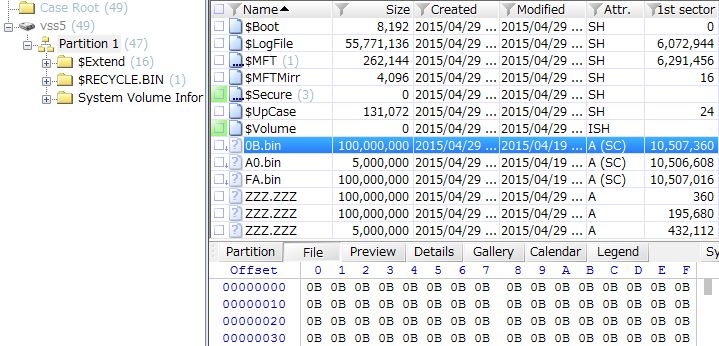
Following is EnCase view of image file 4.
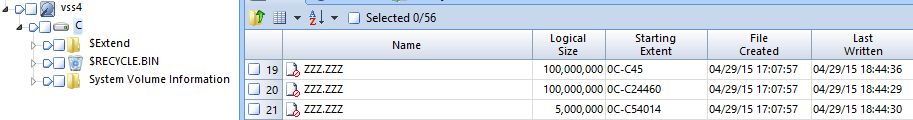
From this point, the contents of 3 files are wiped and names are changed to "ZZZ.ZZZ", but it's possible to recover 3 files from SC. You can extract these data when you use tools which support VSS analysis.
Then I issued the following commands at state 4 respectively.
- 5-a. wmic shadowcopy delete
- 5-b. vssadmin delete shadows /all /quiet
Then I created 2 image files 5-a and 5-b of this virtual disk. As far as I compared state 4 to 5-a and 4 to 5-b, there is no difference from the perspective of file system so I called 5-a and 5-b state 5.
SC file and relevant files are changed as deleted after command execution.
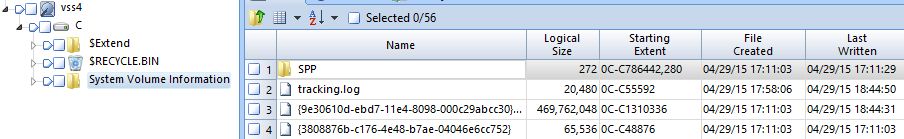
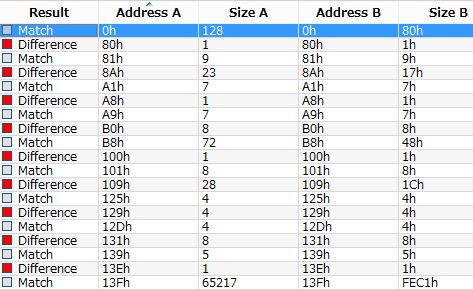
Here is diff result of {3808876b-c176-4e48-b7ae-04046e6cc752} file (i.e. VSS catalog) in hex.
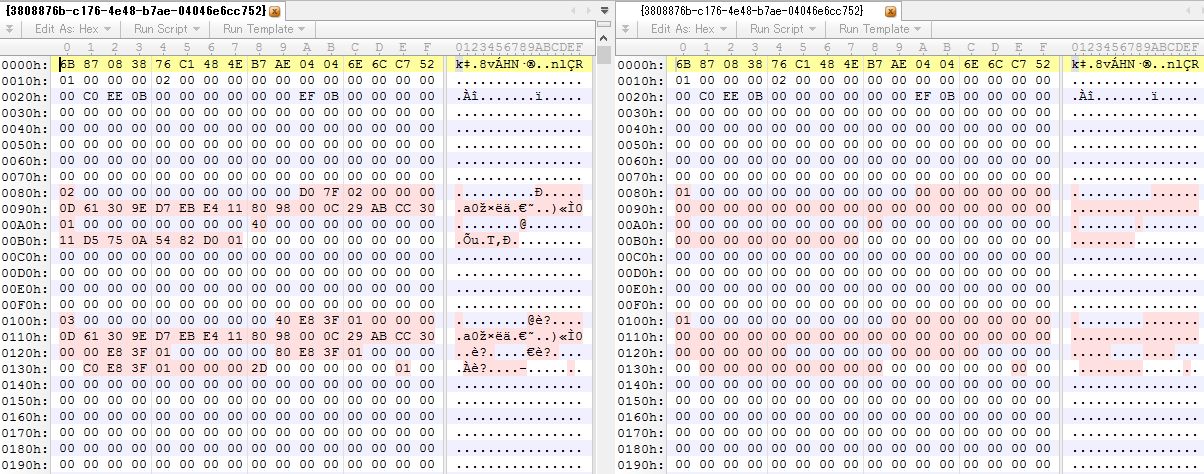
(Left: state 4, Right: state 5)
Red mark means difference and we can see some data was changed to 0x00 in state 5.
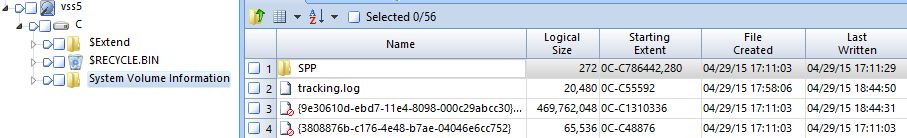
Here is diff result of {9e30610d-ebd7-11e4-8098-000c29abcc30}{3808876b-c176-4e48-b7ae-04046e6cc752} file (i.e. VSS store) in hex.
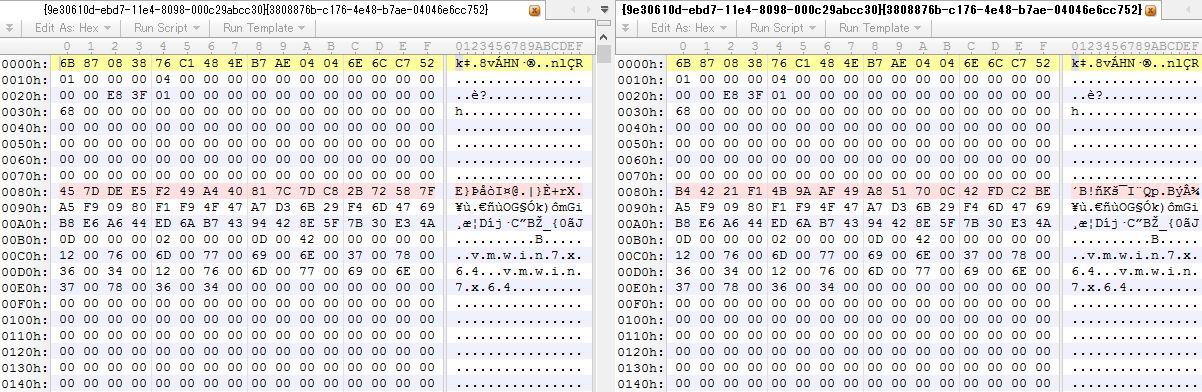
(Left: state 4, Right: state 5)
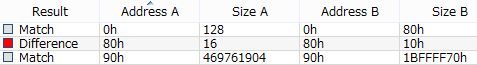
Red mark means difference and we can see 16 byte data at offset 0x80 (128) was changed.
VSS format is described in detail in the following site by Joachim Metz.
Volume Shadow Snapshot (VSS) format
https://github.com/libyal/libvshadow/blob/master/documentation/Volume%20Shadow%20Snapshot%20(VSS)%20format.asciidoc
I tried to make sure of what changed 16 byte data is. I have confirmed 16 byte data at offset 0x90 is "Shadow Copy ID" and 16 byte data at offset 0xA0 is "Shadow Copy Set ID". So these data are described at "4.2 Store information" in his site and unfortunately changed 16 byte data are "Unknown".
By the way we must choose the appropriate approach to recover 0B.bin, A0.bin and FA.bin files from state 5. For example, Shadow Explorer, Shadow Kit and EnCase VSS Examiner are based on a Windows function like vssadmin. It doesn't recognize deleted SC and actually their tool didn't find and recover 3 files.
If you use tools which parse SC itself, it's possible to recover 3 files. At least I have confirmed X-Ways Forensics can recover these files using "Parse volume shadow copies" in Refine Volume Snapshot.
I don't know other tools such as Internet Evidence Finder, ProDiscover and libvshadow support deleted SC.
If you encounter deleted SC by wmic/vssadmin, you can identify the date in prefetch and UsnJrnl. Especially, prefetch stores "\DEVICE\HARDDISKVOLUMESHADOWCOPY#\$MFT" pattern in accessed file list.
There is also the possibility that we can recover the data from deleted SC which is deleted by maximum limit of size. SC is created by Windows scheduler at regular intervals and oldest SC is deleted if the dedicated area reaches maximum limit. Examiners may need to think that they should try to analyze deleted SC deeply.